Contents
TL; DR:
- The document and pdf security industry is, like most industries targeted at large enterprises, still incumbered by old-school ways of thinking and doing document transfer and security.
- While there are some promising document security startups leveraging emerging tech to protect business-critical information, generally speaking – these innovations have yet to achieve mass adoption.
Disclaimer
For the purposes of this article, we’re focusing mostly on the need for organisations to enhance digital enterprise security to prevent sensitive and confidential documents, records and PDFs from being leaked. That said, when talking about enterprise security, you can expect some natural overlap with enterprise security relating to personal data breaches, involving the theft of email addresses or credit card details, for example.
Current Context
General Interest in Document Security
Unless you’ve been living under a cybersecurity rock for the last year, you definitely heard about IBM’s shocking revelation that the average total cost of a data breach in 2018 was around $3.86 million.
Which – yes – is a huge number, and begs the question: how many organisations are actively looking for security solutions to protect the millions of files containing sensitve or confidential information that are shared both internally and externally every day?
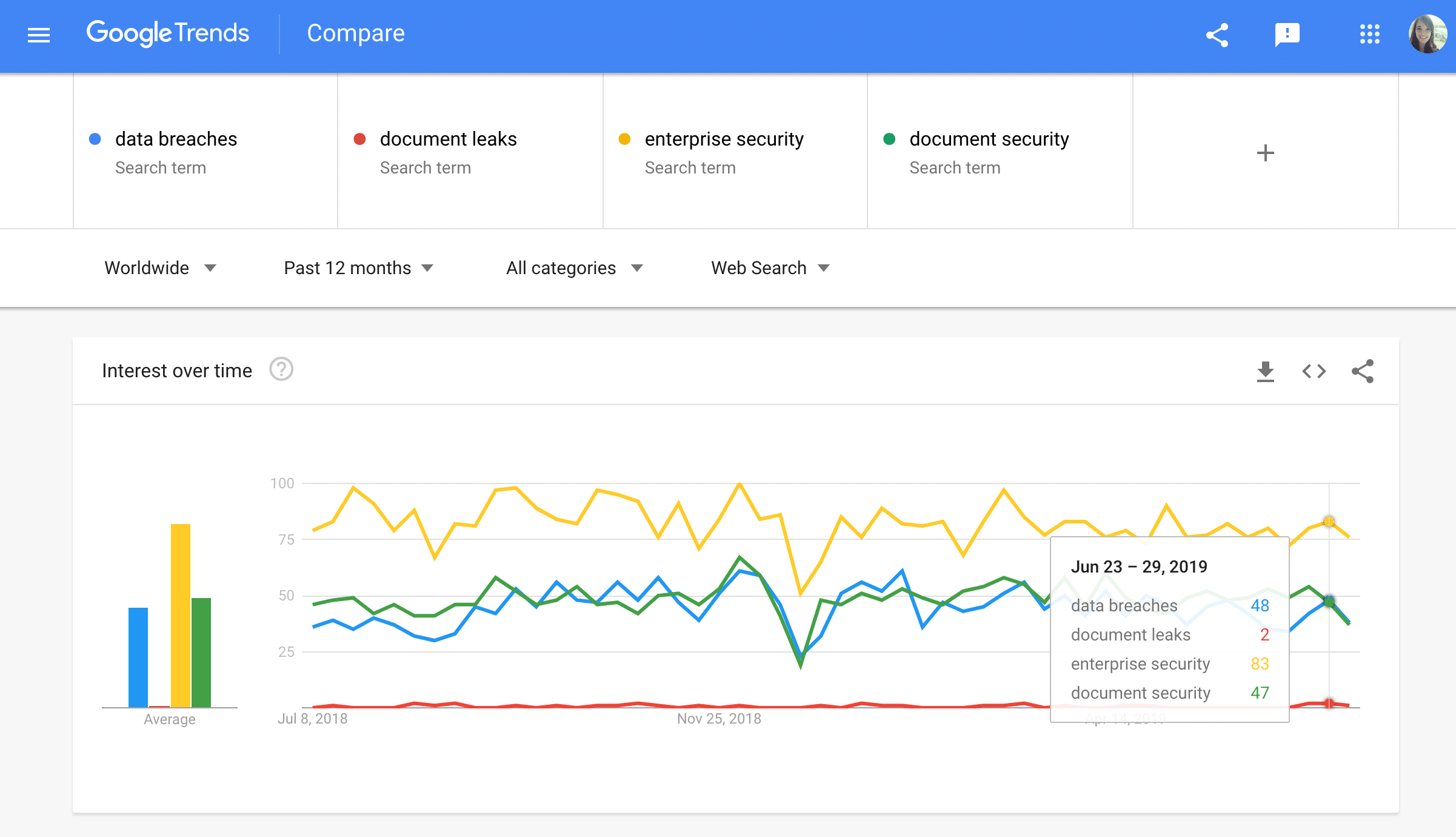
The umbrella term ‘enterprise security‘ (naturally the term with the highest search volume) is a surefire way to hit on content relating to the way large organizations are moving towards protecting their most sensitive data and systems.
For the sake of brevity I won’t go into the details of every search relating to the individual protection of confidential documents like Contracts; Board Minutes; M&A documents; Market, Risk or Competitor Analyses; Internal Investigations…
But: drilling down further into just document security, in the United States, specifically:

Search, Reddit, and Quora Results for PDF Security
One step further, into the Google Search Results for ‘pdf security software‘: 
Redditors are mostly asking about how to get around PDF security encryption; though some are on the side of copyright protection:
On Quora, people are asking the same question – How do I secure PDF files? – but proposed solutions are also of the old-school variety:

This quick desktop analysis, though entirely qualitative, teaches us a few things about the words and phrases people are (and aren’t) using to talk about the need for PDF security software and sensitive document protection.
What’s an Incident Response Plan Anyway?
Another term you can’t throw the phrase enterprise security around without hitting on the head is ‘Incident Response Plan.’
— See: Interzer’s Building your bullet proof response plan [white paper]
Interzer advocates a four-step approach to cybersecurity incident response plans; but at Custos we’ve actually managed to cut this process down to three:
“Data breach mitigation has 3 critical components:
-
- Protection: products and procedures to limit the illicit spread of data
- Detection: finding leaked content on- and offline, and identifying sources
- Response: plugging leaks and mitigating damage
The limit of protection technologies is that at some point the data needs to be readable by a human. At that point, someone that wants to leak data cannot effectively be blocked from doing so using technical means. A full 48% of data breaches resulted from criminal or malicious human action, frequently from insiders.
When you have someone on your team that wants to leak data and are confident that they won’t get caught, they will succeed.
That’s where detection comes in.
Rapid detection of breaches is the most effective lever to reduce direct and indirect damage. On average, it currently takes almost 200 days to detect a data breach. Imagine your competitor knowing your designs or plans, or criminals getting your customer data, more than half a year before you can start reacting.
Typically breaches are only discovered when data is found on the public internet, whereafter it takes on average a further 70 days to respond to the leak. No wonder leakers like the bad apple mentioned above are not afraid of being caught.
This is where the Custos technology comes in.
The Custos solution integrates with existing information management platforms or workflows, and adds a unique watermark and blockchain bounty to each copy of a document that is distributed.”
Emerging Tech Solutions to the Document Security Problem
BitTorrent
— BitTorrent (BTT) [white paper]
- Tokenizing the world’s largest decentralized file sharing protocol with BTT. The BitTorrent protocol, created by BitTorrent Inc., facilitates the exchange of files between untrusted parties. Its primary limitation is that collaborations between parties using the protocol cannot persist over time, inhibiting the exchange. Blockchain technologies allow for collaborations between untrusted parties to persist over much longer periods of time. BitTorrent has the ecosystem and expertise necessary to integrate blockchain technologies into the BitTorrent protocol. Doing so would both eliminate the protocol’s existing flaw as well as open up a new borderless economy in exchanging value for computing resources on a global scale.
Filecoin.io
— Filecoin: A Decentralized Storage Network [white paper]
- The Filecoin network achieves staggering economies of scale by allowing anyone worldwide to participate as storage providers. It also makes storage resemble a commodity or utility by decoupling hard-drive space from additional services. On this robust global market the price of storage will be driven by supply and demand, not corporate pricing departments, and miners will compete on factors like reputation for reliability as well as price.
Authpaper.io
— Authpaper Delivery: Blockchain-based system for data delivery and certifications [white paper]
- Authpaper Delivery combines blockchain, BT, cryptography and other current technologies to build a peer-to-peer digital data delivery platform. All data delivered is confidential except the specified recipients. Data is verified to be unchanged down to every single bit. Operations on the data are properly done and recorded among the peers so that the delivery histories are public verifiable yet unforgeable. Peers are rewarded by delivering the encrypted pieces of digital data and helping to run the platform with good will.
Custos Media Technologies
— Why watermarking is not enough – how blockchain technology can be used to stop online piracy [white paper]
- Media owners trust Custos to keep sensitive media safe, and to detect leaks when they happen. Using a combination of imprecepticle forensic watermarking and blockchain-based content tracking, Custos prevents the illegal redistribution of PDFs, sensitive documents, ebooks and educational content, and video files.
Industry Standard Security Features
Existing and Incumbant Document Management Platforms
— Adobe Acrobat DC with Document Cloud services security overview [whitepaper]
- Executive Summary — this whitepaper describes the defense-in-depth approach and security procedures implemented by Adobe to enhance the security of their document management software suite.
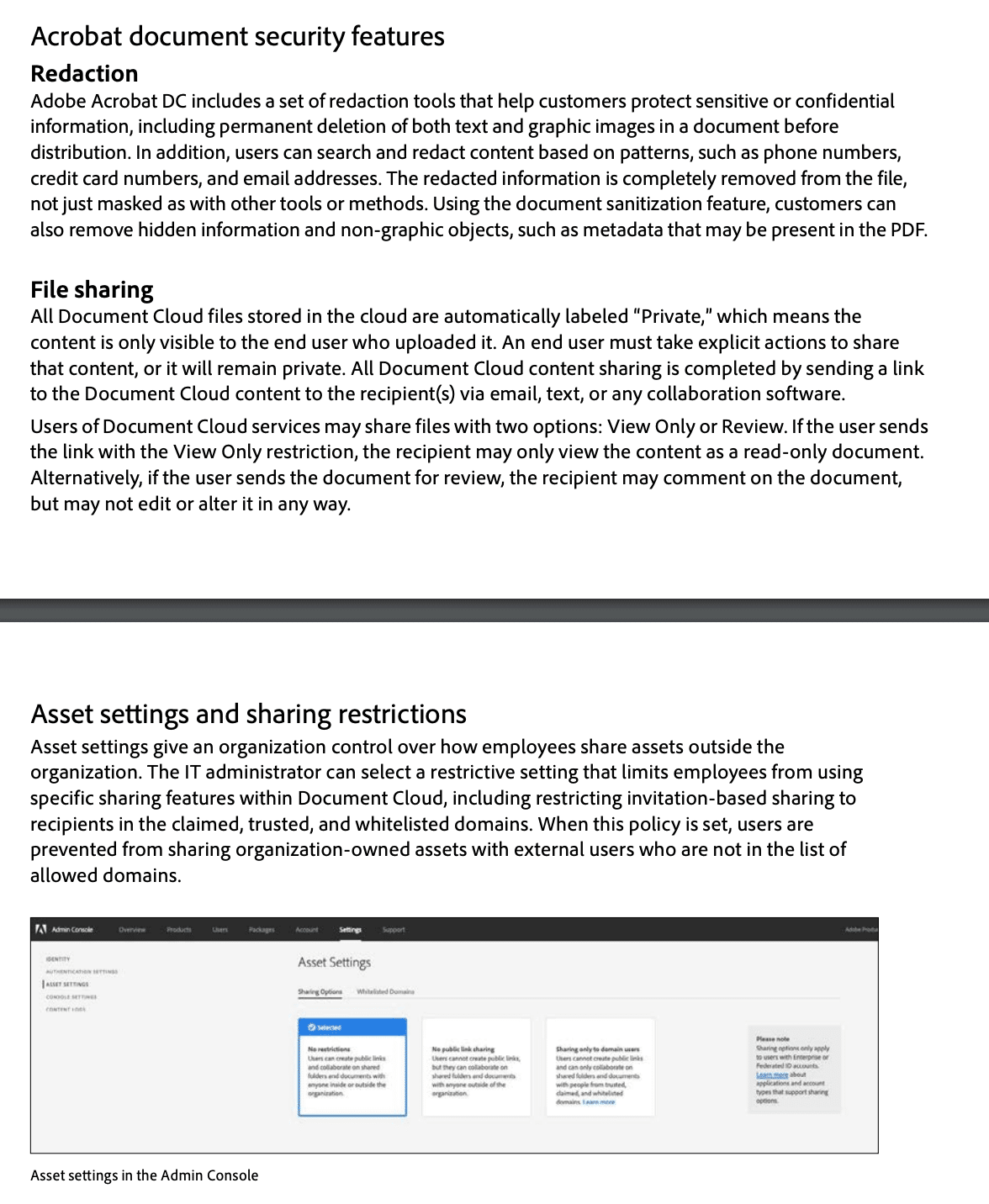
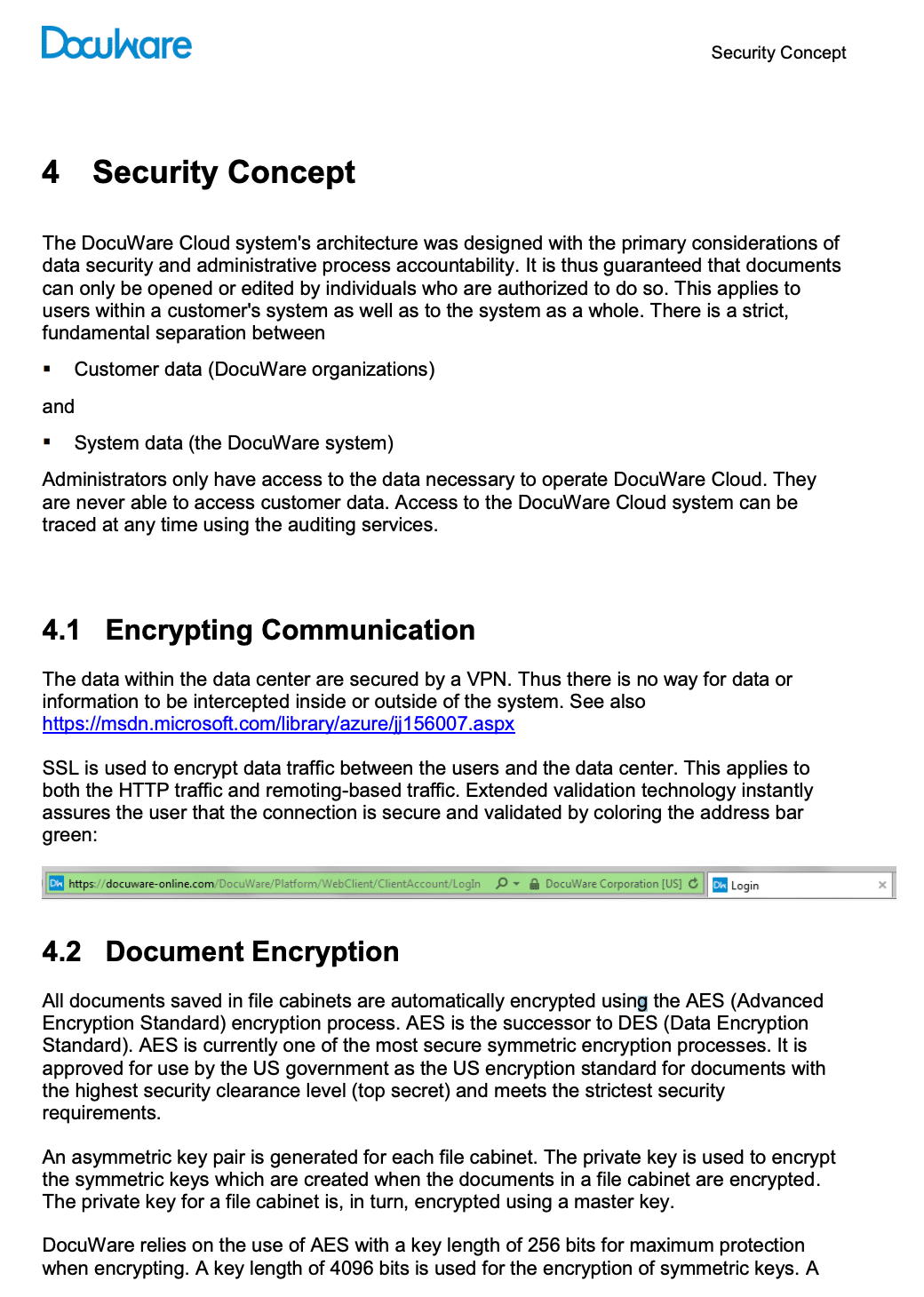
- Executive Summary — This white paper presents the measures which have been implemented for data security and fail-safety. It includes all preventive measures against accidental or deliberate manipulation of managed content, and against data loss. Security features also include measures that guarantee data protection and ensure that changes within the system are traceable. This should provide readers with a technically sound understanding of the DocuWare Cloud system’s structure and security. This white paper addresses clients (users), consulting companies, IT magazines, and distribution partners. It assumes a certain level of technical knowledge about the structure of modern software applications, ideally of document management systems. Detailed knowledge of current or previous DocuWare versions is not necessary.
News and Blogs
With privacy-violating evil-corp boogeymen, hackers, and governments posing behind potential terror threats covered in mainstream media on the daily, it’s no surprise businesses are too scared to share confidential corporate documents and sensitive data online.
— Why is Physical Mail Still Being Used to Share Sensitive Documents? by Kirill Shilov
- TL; DR — a look at emerging technical solutions that are meant to offer new ways to send files, data, and documents over the internet without putting the data they contain at risk. Includes Authpaper Delivery, BitTorrent, and Filecoin; argues they’re superior in terms of security than all other centralized solutions available at the market today.
— How Executives Can Better Prevent Data Breaches In Our Digital Day and Age by Drew Rossow
- TL; DR — highlights astronomical cost of data breaches; argues “data breaches are preventable, and as an executive you have the responsibility to make sure they don’t happen. Here’s how you can mitigate the risk.” Explores solutions including correct staffing, clear accountability, employee education, and prevention.
— Remembering 2018’s Most Prominent Data Breaches by Aaron Gershwin
- TL; DR — Covers Facebook’s Cambridge Analytica, the Marriot Hotel Data Breach, and the Aadhar data leak.
— Data breaches: how they affect people and what can we do to fight them by Maria Paula Fernández
- TL; DR — “Only in 2018, people have been victims of 1,293 total data breaches, compromising more than 174 million records, in companies such as FedEX, the sportswear brands Adidas and Under Armour, Saks Fifth Avenue, crypto exchanges such as Bithumb, Ticketmaster, Air Canada, T-Mobile, and the list goes on… We can’t remain ignorant to the fact that we need tools to protect existing software, and new software built, with the consumer in mind, to combat decades of abuse. We need tools built by technologists who know the bells and whistles behind cyber attacks, who understand how valuable it is to have secure hardware, who value their users with their data and dedicate their practices to this.”
— The Best Document Management Software for 2019 by Tim Ferrill
- TL; DR — Businesses generate a lot of data — choosing a reliable and scalable DM system is key to streamlining and automating workflows. Storage, Archiving, version control, workflows, access permissions, backup, and data protection can all be handled by a DM solution. It is the starting point for storing, securing, and sharing various business documents. Compares 10 Document Management options, including Microsoft Sharepoint Online and Docuware Cloud.
Additional Reading
— Deloitte Review: The hidden costs of an IP breach
- TL; DR: “Given their importance to growth, market share, and innovation, IP and cyber risk should rightly sit with other strategic initiatives managed at the C-suite level.”
- Deloitte advices enterprises to ask the following questions:
- Where is it possible to reduce the number of people with access to IP?
- Where are the most vulnerable links in the routine handling and protection of IP?
- Is the company’s data management/protection strategy sufficient and well understood?
- Are cyber monitoring capabilities aligned and prioritized to detect threats against the company’s most strategic IP assets, including fully leveraging private sector–government cyberthreat sharing capabilities?
- If the company’s innovation ecosystem extends to partners, suppliers, or third parties, have controls and policies been appropriately extended beyond corporate borders?
- Are well-meaning researchers or developers knowledgeable about the company’s storage, data management, and retention policies so that information is not carelessly left exposed?
— The WIRED Guide to Data Breaches
- TL; DR — While mostly focusing on personal data breaches involving information like names, email addresses, passwords, Social Security numbers, dates of birth, credit card numbers, banking data, passport numbers, phone numbers, home addresses, driver’s license numbers, medical records, the article supplies a great list of further reading on big-name data scandals involving Yahoo, Facebook, Equifax, Marriot, and the like – if you’re keen to go down a data breach rabbit hole.
- WIRED’s advice to institutions? (Editor’s Note: No mention of looking to emerging tech for a solution?)
-
- Lock It Down: Require users to set up strong, unique passwords and two-factor authentication to access network services.
- Keep ‘Em Out: Implement access controls so everyone can’t access everything. Users should only be able to see the content and applications they need.
- Slice It Up: Segment enterprise networks so that sensitive data and operations run in different digital areas and aren’t accessible from parts of the network that are low-sensitivity.
- Update It Quick: Apply software updates as soon as they’re available. For real.
— IBM’s 2018 Cost of a Data Breach Study: Benchmark research sponsored by IBM Security; Independently conducted by Ponemon Institute LLC Global Overview
- TL; DR — The global average cost of a data breach is up 6.4% from 2017 to $3.86 million. The average cost for each lost or stolen file containing sensitive/confidential information is also up: 4.8% YOY, to $148.
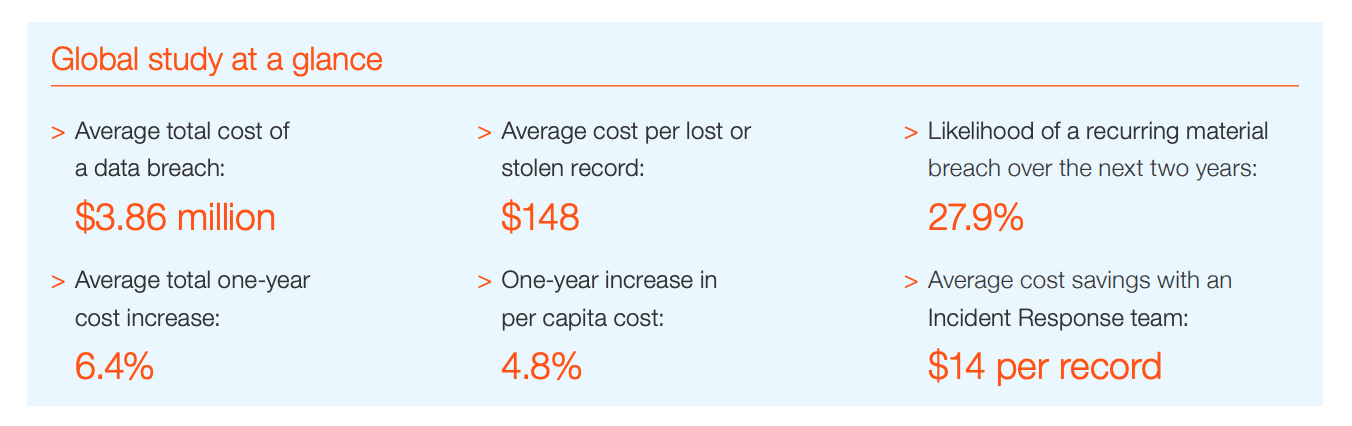
Bonus—3 Podcasts for Enterprise Security Professionals
- A look at the current state of enterprise security solutions, including new products, features, and industry reporting.
— Brakeing Down Security Podcast
- A podcast all about the world of Security, Privacy, Compliance, and Regulatory issues that arise in today’s workplace. Co-hosts Bryan Brake, Brian Boettcher, and Amanda Berlin teach concepts that aspiring Information Security Professionals need to know, or refresh the memories of the seasoned veterans.
— The Crypto-Gram Security Podcast
- Audio of Bruce Schneier’s monthly Crypto-Gram security newsletter.

P.S. Why prevention is better than cure

Go straight here if you’re looking for document security software
- Once integrated, Custos’ Core technology embeds a unique, imperceptible watermark into your PDF file each time it’s downloaded by somebody inside or outside of your organization.
- Should that document, record, or PDF be part of a data breach and located somewhere it shouldn’t be online, that watermark can later be used to pinpoint the exact identity of the user within your distribution network who downloaded the copy of the orginal file.
- In addition to using blockchain-based tracking to help you trace damaging, confidential file downloads and leaks, Custos can inform your network of the presence of embedded forensic watermarks, each time you share a file with anybody, in order to deter leaks – because prevention is always better than cure.
+27-21-808-9505
[email protected]
Twitter: @custostech